Network Segmentation Part 1
Finally, I decided to start segmenting my network, mainly for the reason of connecting IoT sensors to it over which I do not have full control and which are known to get outdated and vulnerable quickly. Furthermore, I want to create a separate network for my internet facing server group. I recently restructured a little (see old network), but I was not happy with it and switched back to a non virtualized router.
I will try to wrap it up in two parts. Firstly the hardware and general configuration part and secondly the thoughts and implementation of the segmentation in the router with the necessary firewall rules.
I will try to link the most important terms to explanations in the footnotes.
Hardware
One needs a router which is smart enough for this task. Meaning you should be able to create different VLANs1, tag them accordingly and also a convenient way to introduce firewall rules. I already have a working opnsense router, which also acts as DNS and DHCP server. One also need at least two ports, one for the incoming WAN and one for the outgoing LAN or trunk2. If you have more than two ports you could also use a simpler switch and go without a trunk, but with multiple physical links.
Furthermore, one needs a switch. I decided to get a manageable switch which was affordable, small , power efficient and brings VLAN tagging protocols, to be able to make trunk ports. I absolutely needed this feature to be able to make trunk ports, so that I can connect the router and the switch with one cable. For that I bought a Netgear GS108Tv3, which fits in nicely, and I also like the Netgear web interfaces (nothing fancy but somehow intuitive).
Configuration
Router
I am using an opnsense Router. But in my opinion the steps are similar on other software. The opnsense documentation is exceptional, and I would always start there with a task like this. I only summarize a little what I did, because one has to look up the details in the respective software documentation.
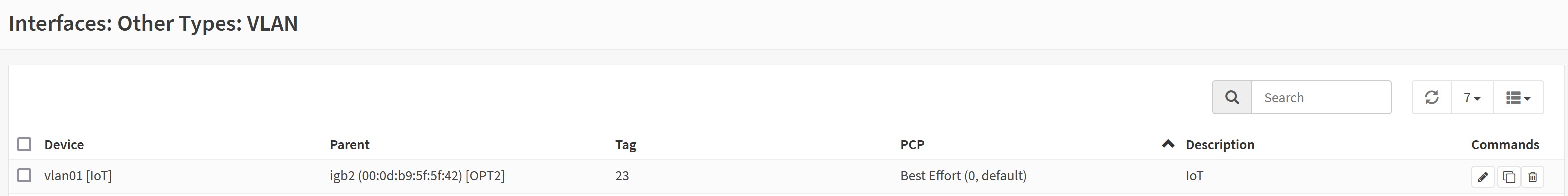
Creating a new VLAN
In opnsense I had to create the VLAN by giving it a name and decide on the number which will be tagged and on which physical interface it will be.
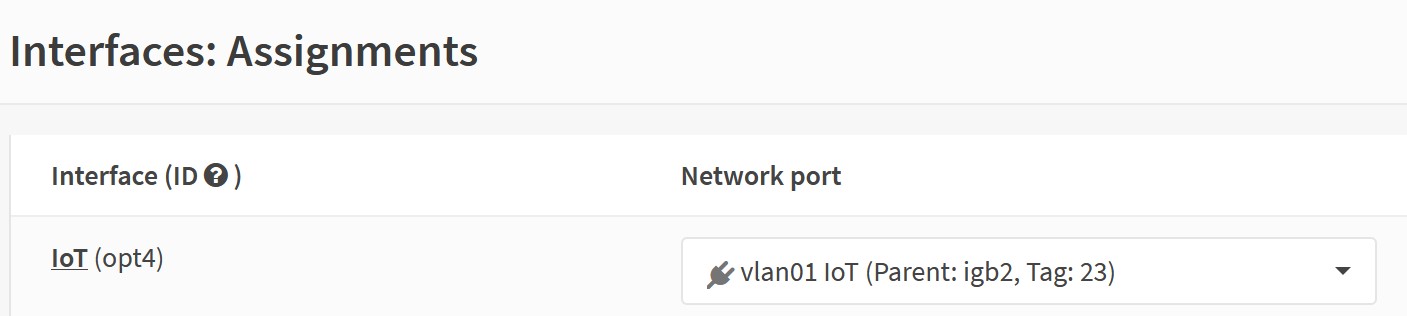
Then assign an interface:
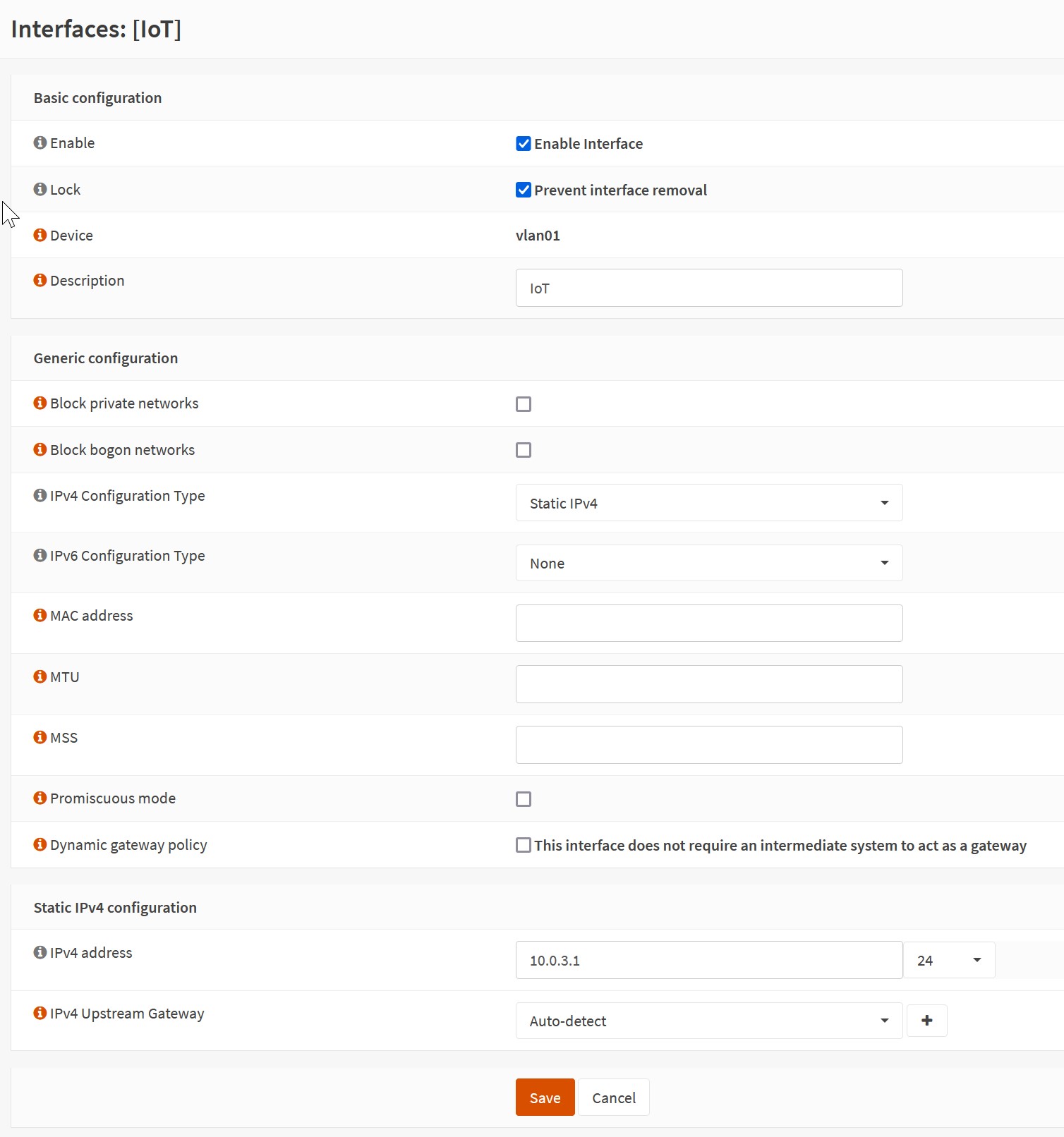
Configure the interface:
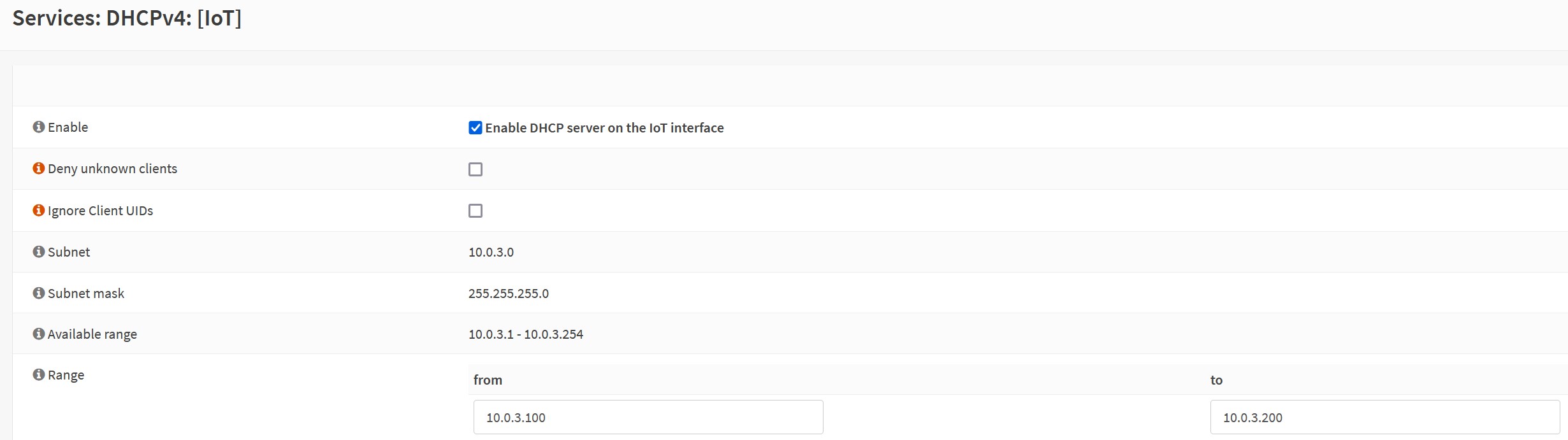
Configure the DHCP server, if needed:
As a starting point to set everything up we will just allow all traffic on this interface. In part 2 I will think about the necessary firewall rules. So that is only for the testing phase:
Switch
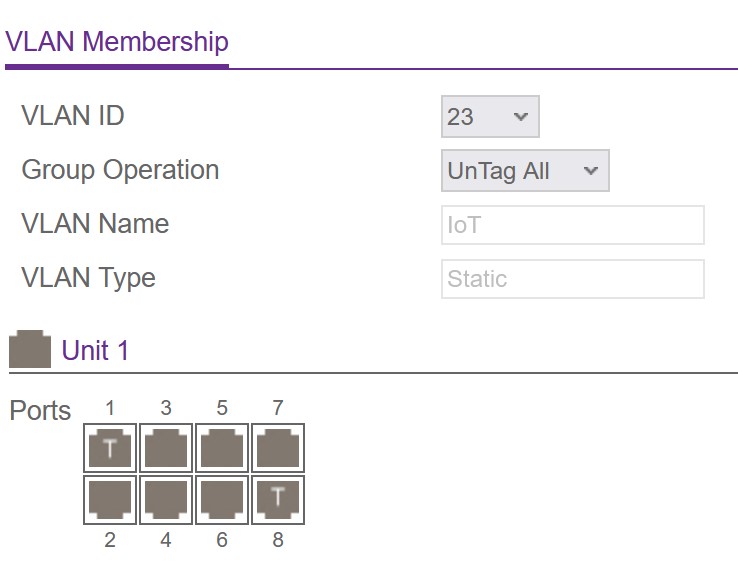
On the switch I also configured the VLAN with id 23 like above. Then you have to assign the VLAN to the ports either tagged or untagged. In the beginning, I struggled a little with this part… I try to explain it a bit more here so that others and my future self can get started or remember easier.
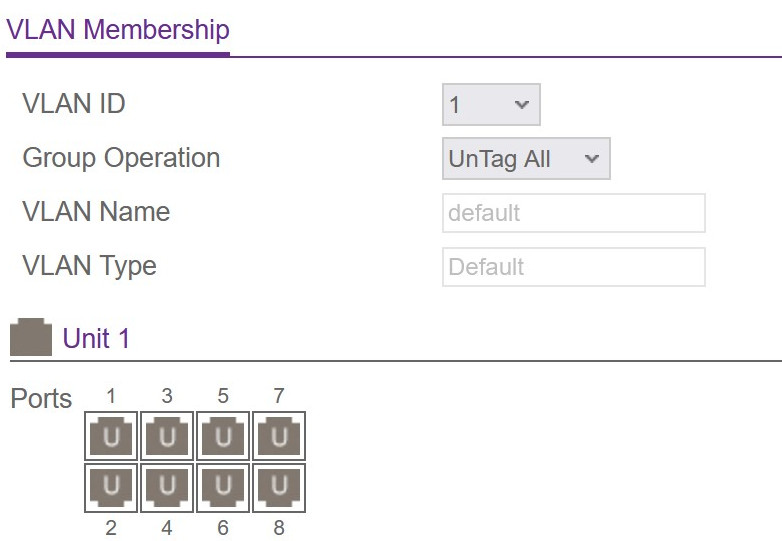
On the switches the defaults will be like everything is untagged VLAN ID 1 and PVID3 1. It will be presented similar than in this picture, if you have a graphical interface:
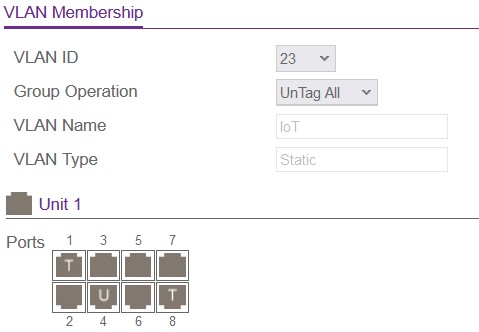
That is fine as long as you only have trunk connections. Like that if an untagged package arrives it will be tagged with ID 1 and thereby belong to the VLAN 1. Every other VLAN will have an overlay with specific tags, so that if a tagged package with for example ID 23 arrives it will be only visible to this VLAN. In this example I have tagged two ports with the new VLAN ID 23. One is the incoming trunk from the router and the other is the outgoing trunk to my access ponit, which then has a specific WLAN for my IoT devices.
If you want a port based VLAN you would need to make a port Untagged with your VLAN ID and also set the PVID to this ID, so that all packages arriving at this interface will be tagged with this ID. Then you can connect any device to this port and, it will participate in only this VLAN.
LAGG
In the switch’s configuration I stumbled over the term LAG. I didn’t know about it, but it certainly sounds interesting for future improvements:
LAGG stands for Link Aggregation Group. It is a method of bonding multiple network interfaces together to form a single,
logical interface. The purpose of this is to increase the available bandwidth and provide redundancy in case one of the
physical interfaces fails.
-
VLAN stands for Virtual LAN. It is a way to segment a physical network into multiple logical networks, without the need for multiple physical infrastructure. This allows for better organization and security of the network by isolating different devices and services from one another, while still allowing them to communicate over the same physical network.
VLANs work by tagging packets with a VLAN ID, which is a number that identifies which VLAN the packet belongs to. This tagging can be done in different layers of the OSI model, most commonly on the data-link layer (layer 2) where the MAC addresses reside. ↩
-
A trunk refers to a link that is used to carry traffic for multiple VLANs between network devices. It is essentially a pipe that connects two network devices, such as switches, and allows them to exchange VLAN-tagged frames. ↩
-
PVID stands for “Port VLAN ID.” It is a term used to refer to the VLAN ID that is assigned to a specific port on a switch.
When a frame is received by a switch, the switch looks at the frame’s VLAN tag (if it has one) to determine which VLAN the frame belongs to. If the frame does not have a VLAN tag, the switch will use the PVID for the port on which the frame was received to determine the VLAN that the frame belongs to.
The PVID is typically used for untagged frames, or frames that do not have a VLAN tag. In this way, it acts as a default VLAN for the port. Many switches have a default PVID of 1, but this can be configured to be any valid VLAN ID.
It is also possible to have multiple vlans assigned to a single port, this is done by using the concept of Tagged and Untagged vlans on the port. The Tagged vlans are the vlans which are assigned to the port and can have a vlan tag in the frames, whereas the untagged vlan will be the PVID of the port, it will be assigned to the frames which does not have any vlan tags. ↩